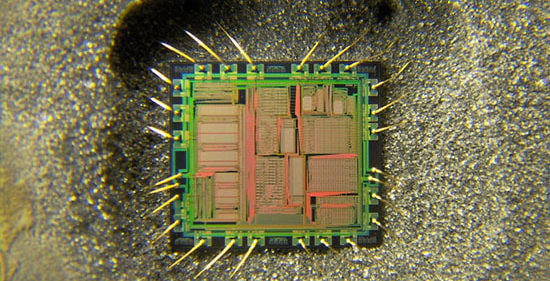
14 Suggestions for IC Encryption
Published by Fast PCB Studio on
14 Suggestions for IC Encryption
Theoriatically, any attacker can use enough of the investment and time to break through the current IC unlock methods. This is the basic principle that system designers should always keep in mind. Therefore, as the design engineer of electronic products, it is very necessary to understand the latest technology of the current single-chip attack, to know ourselves and know what to do, in order to effectively prevent the products that have been spent a lot of money and time hardly designed by others to be counterfeited overnight. occur. We propose the following recommendations based on the Fast PCB Studio Decryption Practice:
(1) Before selecting the encryption chip, it is necessary to fully investigate and understand the new progress of the chip decryption technology, including which ones have been confirmed to be crackable. Try not to use a chip that can be cracked or the same series and the same model to choose a new technology, a new structure, and a short time to market. If you can use ATMEGA88PA, the cost of the current domestic cracking needs about CNY 6K, and it is relatively difficult at present. Decrypted ST12 series, dsPIC30F series, etc.; other can also be combined with CPLD encryption, so the cost of decryption is very high, the general CPLD for decryption is also about CNY 10K.
(2) Try not to use MCS51 series MCU, because the MCU has the highest popularity in China and is the most thoroughly studied.
(3) The original creator of the product generally has the characteristics of large output, so it is possible to use a relatively simple and unpopular single-chip microcomputer to increase the difficulty of pursuing the counterfeiter. Select some uncommon single-chip microcomputers, such as ATTINY2313, AT89C51RD2, AT89C51RC2, motorola microcontroller, etc. More difficult to decrypt the chip, the current domestic development will use the familiar motorola microcontroller is very few, so the cost of cracking is also quite high, from 3,000 to 30,000.
(4) Under the condition of design cost permission, smart card chip with hardware self-destruct function should be selected to effectively deal with physical attacks; in addition, when programming, add time to timing function, for example, use 1 year to automatically stop all functions. The operation will increase the cost of the cracker.
(5) If the conditions permit, two different types of single-chip microcomputers can be used for backup and mutual verification, thereby increasing the cracking cost.
(6) Polish the chip model and other information or reprint other models to make a false mess (note that the reverse side of the LOGO should also be erased, many chips, the decryptor can judge the model from the reverse side, such as 51, WINBOND, MDT, etc.) .
(7) It is possible to use a flag or a unit that is not disclosed by the microcontroller and is not utilized as a software flag.
(8) Using the A5 command encryption in the MCS-51, in fact, all the information in the world, including English data, does not speak this instruction. In fact, this is a good encryption instruction. The A5 function is a two-byte null operation instruction encryption method in A5. Then add a two-byte or three-byte opcode, because all disassembled software will not disassemble the A5 instruction, causing normal program disassembly, and the executable program can be changed without any problem.
(9) You should write in your program area the development time and imitation of your big name unit in order to obtain legal protection; when you write your name, it can be random, that is, use some kind of Algorithm, under different external conditions, your name is different, such as, etc., which is more difficult to disassemble and modify.
(10) Using a high-end programmer to blow off some of the internal pins, you can also use a homemade device to burn the gold wire. This is almost impossible to decrypt in China. Even if it is decrypted, it costs tens of thousands and requires multiple masters.
(11) Sealing the entire circuit board with a confidential silicone (epoxy potting), which has more unused pads on the PCB, and can also be doped with some unused components in the silicone, while the electronics of the circuit around the MCU The component should be erased as much as possible.
(12) For SyncMos, Winbond MCU, the file to be burned will be converted into HEX file, so that the program vacancy programmed into the chip will automatically add 00. If you are used to BIN file, you can also use the programmer to put the blank area. The FF is changed to 00, so that the general decryptor can not find the vacancy in the chip, and thus cannot perform the subsequent decryption operation.
(13) Compared with horizontal encryption, for example, the 18F4620 has an internal phase-locked loop that can generate high-precision clocks by using RC oscillation. The internal data of the 18F4620 is erased when the power is turned on, so that the decrypted file cannot be used at all.
(14) The NEC series MCU is a representative of the Japanese chip. The MCU has designed sufficient protection measures to ensure the security of its program code. At the same time, the MCU has no PROGRAM READ function, so the program cannot be read by the programmer.
(Note: The verification function when programming the chip with the programmer is not to read the program for verification, but the programmer sends the data to the chip, and the chip core independently compares the data with the memory area, and then compares the result. Return to the programmer).
Of course, in order to fundamentally prevent the MCU from being decrypted, it is impossible. The encryption technology is constantly developing, and the decryption technology is constantly developing. Now, no matter which MCU, as long as someone is willing to pay for it, basically can be made, but only At the cost and length of the cycle, programmers can also protect their development from legal sources (such as patents)